

pcapdroid (available from Google play) is a wireshark-like packet capture tool for android devices. There’s a few advantages to having packet capture running on the actual device for troubleshooting, debugging, keeping an eye on suspect apps and what they’re doing in the background etc. It can export in csv and wirreshark formats, and supports decrypting SSL/TLS packets via a plugin.
In fact it already has some paid features available for malware detection using blacklists and use as a device firewall.
One of the great things about it is it that because of the way it’s designed it doesn’t need a rooted phone to work – it does have some extra features for devices with root access – but it works fine without. So if you have apps (or policies) which require that your device remains unrooted then it will play nicely with them.
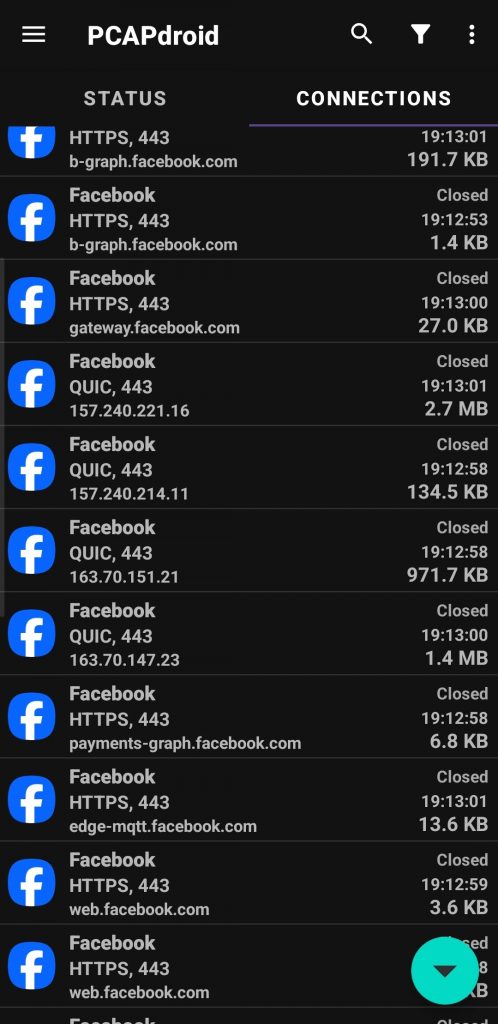
In order to capture packets it sets up as a VPN on the device and watches everything passing through it, you can filter packets captured to a particular app from a list of all apps installed on the device and filter the results by various factors including hostname, ip etc.
It also has a man in the middle option (MITM). This installs a certificate locally and a plugin to decrypt SSL/TLS connections which allows you to intercept encrypted connections from apps and decrypt the packets. The certificate seems to be accepted by most apps, although some apps will not trust user added certificates (this is where having root access will help as you can add to the trusted certificate list), and some apps will only trust from their own inbuilt list of certificates. Importantly the certificate can be removed and easily re-installed when needed from within the plugin.
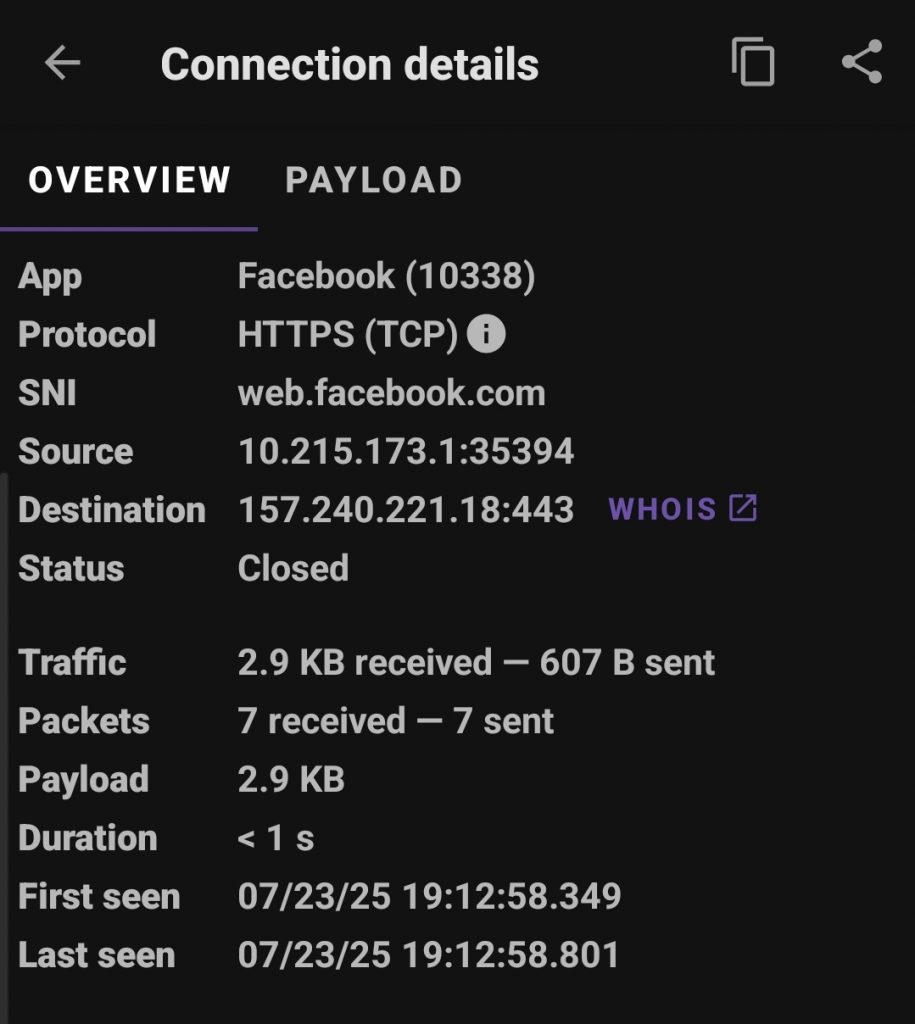
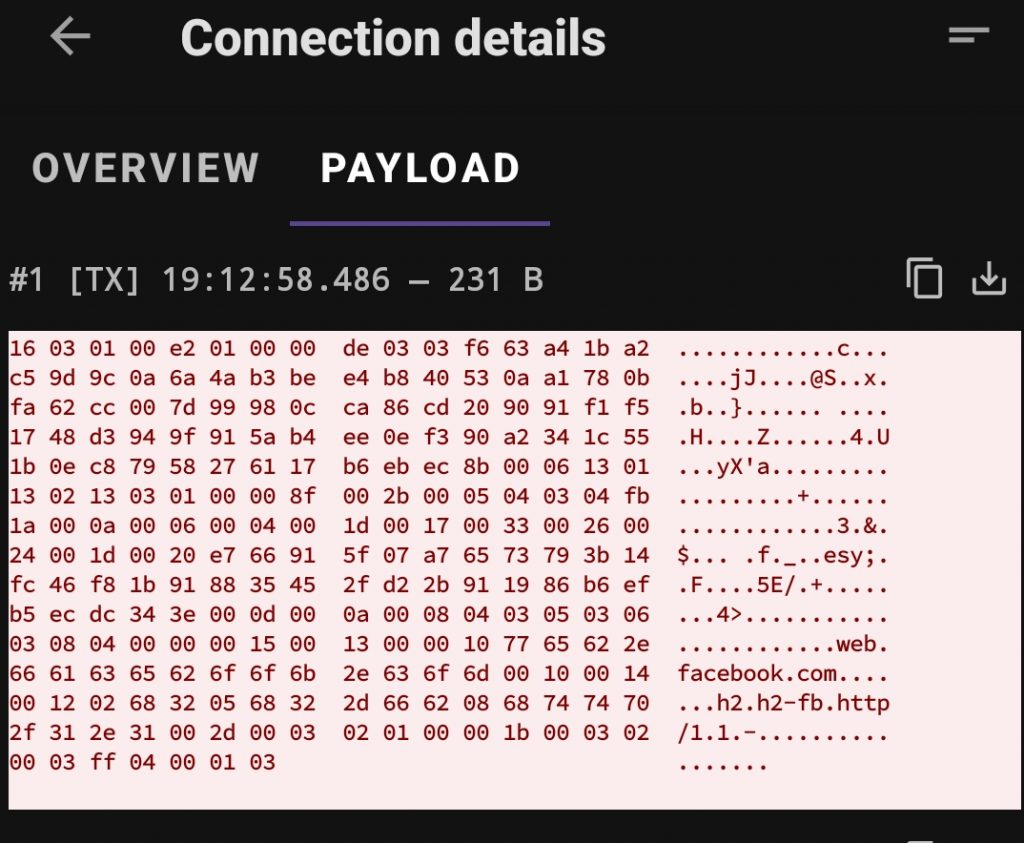
As an example, there’s a particular API I wanted access to, it’s open to the public but there’s no official documentation of it’s endpoints and what info there is available on it is quite limited. There is however an app which uses the API so by intercepting the requests from the app using pcapdroid I was able to see exactly what endpoints and what parameters it was using to access the API.
[image showing requests with [redacted] endpoints]
We can filter the capture by app limiting it to the one we’re targeting, create a decryption rule for the hostname of the API I wanted, run the ‘capture’ and use the app as normal. You can enable full payload capture to get everything from the body of the responses but just the requests and headers were enough for me to get the endpoints and was able to work out what parameters are available on each. With a little playing around with curl to see how various parameters control the response and format I was able to map out the API.
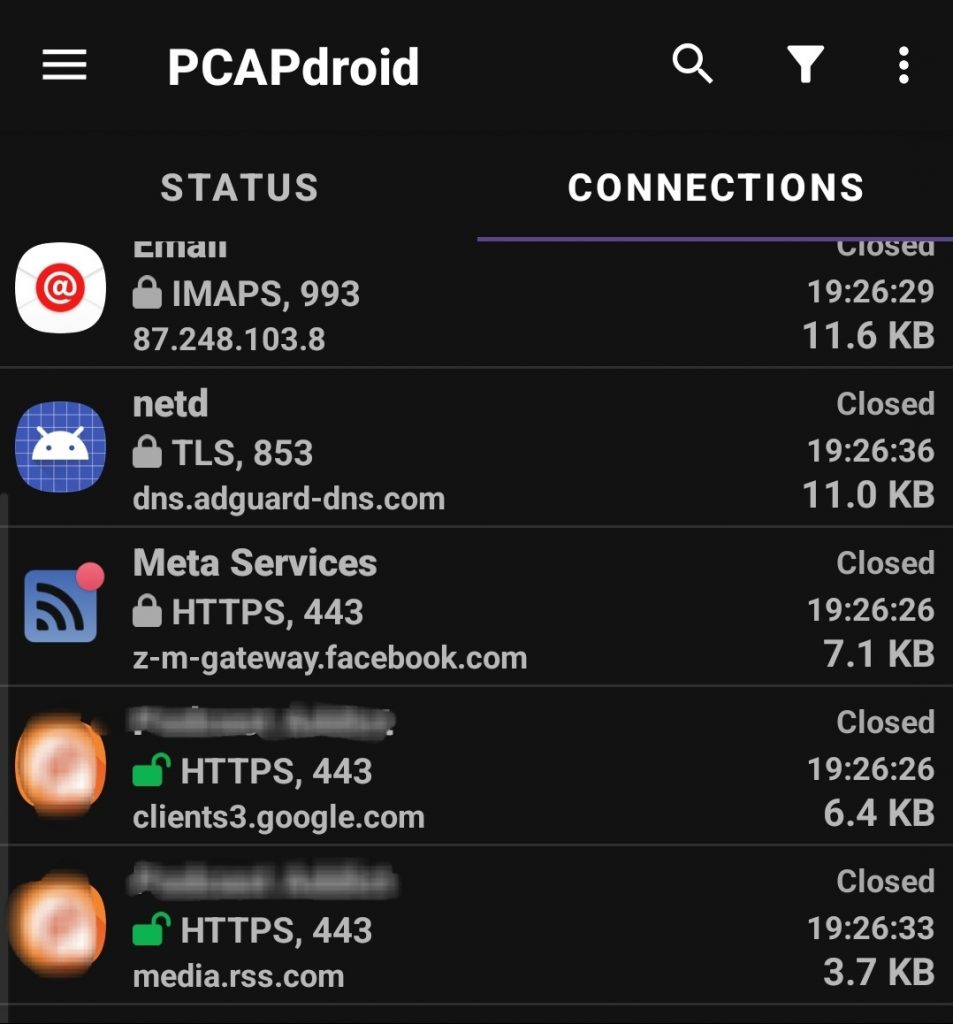
The green padlocks indicate where the mitm proxy has succeeded in decrypting the packets, the grey padlocks indicate packets which were encrypted but were not decrypted because we haven’t added a rule that included them. If there is a failure in the decryption this will be indicate by a red padlock and a note on why the deceyption failed.