This machine was added to htb a couple of weeks ago, it’s been rated as easy
Starting with nmap and the address given for the machine we find ports 22 and 80 open, nothing unusual looking on the scan.
The website on port 80 seems to be a company site for a web design firm, there’s some photos, a few names to note down for later, and a contact form – but nothing that seems to lead anywhere.
Start dirb scanning- doesn’t seem to find much interesting, there’s not much on this site.
Scan for subdomains with wfuzz- ah, theres a “dev.” subdomain, looks like a slightly different version of the main site, and has a robots.txt – some interesting files to check out in there
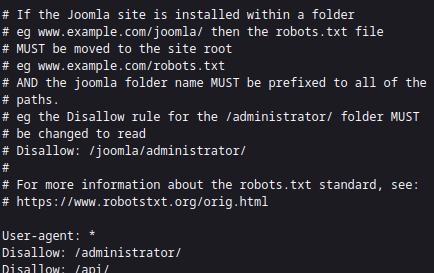
plus the comment at the top tells us something about “joomla” which appears to be a content management system. A quick google and I find out that the version string can be found in an xml file. Looking up the version on exploitdb and it is listed as vulnerable – there is a proof of concept python script on there, it seems that the joomla config is exposed through a link. We don’t need to use the pre-written POC script we can just load the link ourself.
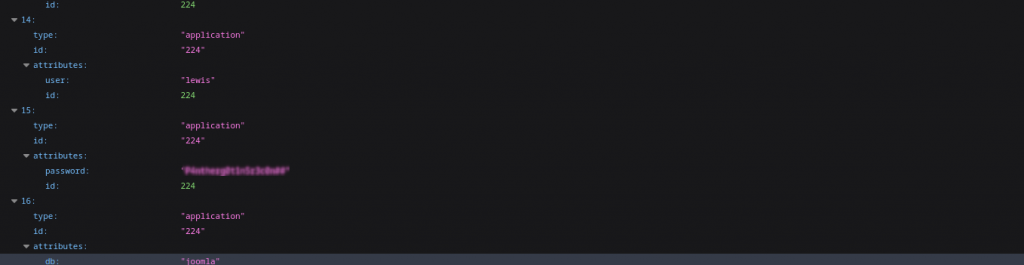
Here the username and password for the database is exposed, what are the chances that the same details can get us into the website admin page? It’s an ‘easy’ box so pretty high I’d guess, and:
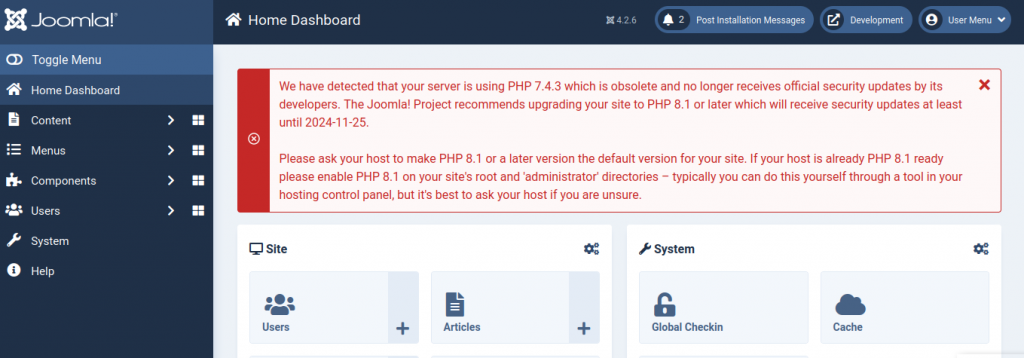
I don’t know my way around this “joomla” but there’s access to the page templates here so I add a reverse shell to the php section and we’re in as the www user account.
Now to get an actual user account, /etc/passwd shows a user account for a “logan”, we have the user/pass for the mysql database from eariler so lets have a look in it:
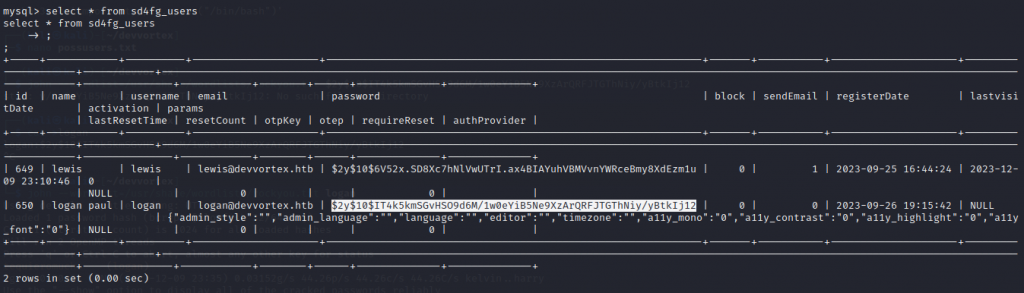
Here’s a hashed password for a user “logan”, might be worth trying to crack it. My computer is a potato but this htb machine is rated as easy so I figure I’ll run JtR on it and if it’s meant to be cracked it’ll be a simple one, else I’m looking in the wrong place, so I start the cracking tool and go off to do something else
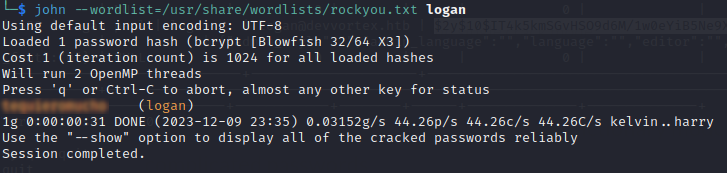
The password was cracked pretty quick so that must be the intended route, try and ssh in as “logan” and yes we have the user flag!
Now to get root:
sudo -l; tells us that we have permission to run the command apport-cli as root.
apport-cli -v gives us the version available, and cross checking online shows that this version is vulnerable to CVE-2023-1326
Simply put: if we can generate a crash report within apport-cli we can view it as a text file before sending, the program uses the less command to display the text file but doesn’t drop it’s privileges so as we can run apport-cli as root, we can run any command from within less with root privileges; read files, modify configuration, even open a shell as root user. For this machine we only need to get the flag from /root/root.txt.
We can cause a report to be generated by running apport-cli -f and a process id (doesn’t matter which, we don’t care about the report only that we can view it). Choose the option to view it and once it’s displayed we can hit “!” and enter our command.
This was a fun machine, pretty straightforward with some unpatched software and a bit of password reuse. It’s classed as an “easy” machine, and it was exactly that.